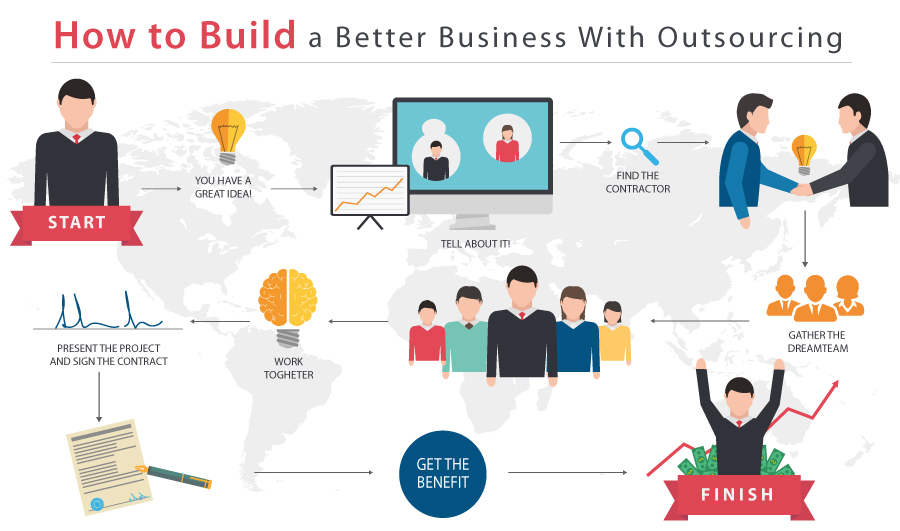
Recent Posts

10 Essential Tools Every Penetration Tester Must Have in Their Arsenal
1,091 ViewsIntroduction Penetration testing or pen testing is an authorised, simulated cyber attack on a computer system performed to evaluate…

Maximizing Conversion Rates with Magento 2 Cash On Delivery Suite Extension
1,270 ViewsIn the dynamic world of e-commerce, one of the paramount challenges businesses face is converting visitors into paying customers….

The Importance of Social Media Management: Benefits that Can Help Your Business Grow
1,217 ViewsSocial media has become an integral part of modern communication and business. It provides a platform for individuals and…

Strengthening Website Security to Ensure a Safer Online Journey
851 ViewsWebsite security has arisen as a critical concern in our increasingly linked digital society. Websites are critical communication, transaction,…

The Progression of Blockchain Technology and its Potential Applications
849 ViewsBlockchain technology, initially introduced as a digital ledger for various cryptocurrencies such as bitcoin, has evolved into a revolutionary…
Why and How to Create Online Waiver Form for Your Services
867 ViewsNavigating the digital landscape can be daunting, especially regarding essential legal documents. Whether you’re a business owner, event organizer,…

How Do Docking Station for Laptops Revolutionize Work with SourceIT?
950 ViewsIn the dynamic realm of modern work, where versatility and efficiency drive success, Docking Station for Laptops emerge as…

Local SEO: Driving Foot Traffic in the Digital Age
1,084 ViewsIn the hyper-connected world, firms face fierce competition to attract online and offline clients. However, digital marketing strategies have…